Explain Different Kinds of Online Threats Brainly
Media Convergence simply refers to the merging of different types of mass media such as Traditional Media Print Media Broadcast Media New Media and the Internet as well as portable and highly interactive technologies through digital media platforms. If a multipartite virus attacks your system you are at risk of cyber threat.

Must Know Online Threats And Prevention Tips Wazile Inc
Cyber threats sometimes feel unrelenting and are becoming more dangerous every day.

. Simple-unstructured advanced-structured and complex-coordinated. Types of Cyberterrorism Experts place cyberterrorist attacks into three distinct categories. Identity fraud where personal information is stolen and used.
Online threats are malware programs that can target you when youre using the Internet. Some scientists estimate that half of all species on Earth will be wiped out within the next century. Sole trader the oldest form of trading there is its also the simplest and the most common type of business youll findThe clue is in the name meaning that you are solely responsible for everything the business does and youre often known as the proprietor.
Cybercriminals are carefully discovering new ways to tap the most sensitive networks in the world. The prefix crypt means hidden and suffix graphy means writing. All the computers that are developed are not alike rather they have different designs and features.
Actual personal computers can be generally classified by size and chassis case. Up to 30 cash back Cyberbullying refers to all kinds of online harassment including stalking sexual harassment doxxing exposing someones personal information like their physical address online without their consent and fraping breaking into someones social media and making fake posts on their behalf. Thus preventing unauthorized access to information.
What Are the Different Types of Business. -Natural calamities like lightening flood storm earthquake etc. Theft of financial or card payment data.
Technology with Weak Security. While the internet presents users with lots of information and services it also includes several risks. A Trojan horse or Trojan is a type of malicious code or software that looks legitimate but can take control of.
Cryptography is technique of securing information and communications through use of codes so that only those person for whom the information is intended can understand it and process it. -Damage caused due to man-made activities such as riots strikes etc. Some computers have very high capacity as well as working speed.
Pollution climate change and population growth are all threats to biodiversity. Up to 20 cash back Types of cybercrime. They mostly target the legacy systems.
There are various types of injection attacks but the most widespread and dangerous ones are SQL injection attack and XSS attack Cross-Site Scripting. Every computer system requires at least one chassis to house the circuit boards and wiring. Protecting business data is a growing challenge but awareness is the first step.
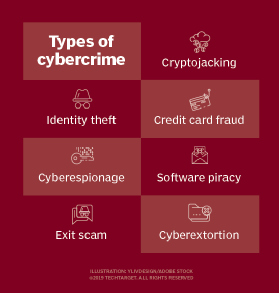
There are at least six different types of business you could choose to start. Communication Computing and Content as all three are integrated. Here are some specific examples of the different types of cybercrime.
The dangers covered are. The 12 types of Cyber Crime. Email and internet fraud.
Overwrite Virus One of the most harmful viruses the overwrite virus can completely remove the existing program and replace it with the malicious code by overwriting it. -Damage caused due to overflowing or bursting of water tanks pipes etc. Trojan horse worms virus spyware are some of the different types of online threats.
Cyberattacks are increasing in sophistication and volume with many cybercriminals using a combination of different types of attacks to accomplish a single goal. A denial-of-service attack floods systems servers or networks with traffic to exhaust resources and bandwidth. It is designed to affect the computer of the victim.
As a result the system is unable to fulfill legitimate requests. These agentsdiseases include ricin toxin Ricinus communis brucellosis Brucella species epsilon toxin of Clostridium perfringens food safety threats Salmonella species Escherichia coli O157H7 Shigella glanders Burkholderia mallei meliodosis Burkholderia pseudomallei psitticosis Chlamydia psittaci typhus fever Rickettsia. New technology is being released every day.
Also known as fixed speech it is the highest form of communicative style which is often used in respectful situations or formal ceremonies like Shakespearean plays weddings funerals and moreIt uses the complex grammatical sentence structure and vocabulary that are only known by experts in that field. Theft and sale of corporate data. The chassis or case is the metal frame that serves as the structural support for electronic components.
This results in the combination of 3Cs ie. The injection attacks are considered so dreadful because their attack arena is super big majorly for the types SQL and XSS. III Personal Computer Types.
In order to protect yourself you need to know about the different ways in which your computer can be compromised and your privacy infringed. Depending upon the requirements computers are being developed. Cryptography and its Types.
Here are the top 10 threats to information security today. However some are slow. This is known as a distributed-denial-of-service DDoS attack.
Attackers can also use multiple compromised devices to launch this attack. These threats have caused an unprecedented rise in the rate of species extinction. Cyberextortion demanding money to prevent a threatened attack.
Gradually it can completely replace the hosts programming code with the harmful code.

Online Threats Impact Physical Safety Ericsson Consumerlab

Top 20 Most Common Types Of Cyber Attacks Fortinet

10 Common Internet Security Threats And How To Avoid Them

Grade 11 Lesson 2 Online Safety Security Ethics And Netiquette By Lyle Kenneth Maclang
What Is Cyberstalking And How To Prevent It

Online Threats Impact Physical Safety Ericsson Consumerlab

Top 5 Internal Data Security Threats And How To Deal With Them Endpoint Protector

Explain Different Types Of Online Threats Brainly In

Explain The Purpose Of Internet Security Explain The Different Kind Of Online Threats Brainly In

What Is Cybersecurity Why Is It Important Built In

Must Know Online Threats And Prevention Tips Wazile Inc

Cybercrime Which Ones Are The Most Common Threats Today Red Points

Explain Different Kind Of Online Threats Class 10 Answer Fast Don T Spam Brainly In

Online Threats Impact Physical Safety Ericsson Consumerlab

The Five Phases Of The Threat Intelligence Lifecycle Flashpoint

Online Threats Impact Physical Safety Ericsson Consumerlab



Comments
Post a Comment